You may or may not have heard of Defray ransomeware before. Apparently, it’s not hit Asian shores as yet but its only a matter of time. The threat is real and so far, they’re targeting the US and EU, for now!
As you may already know of the recent ransomeware attacks purposely being targeted towards healthcare and education industry, they (the criminals) are getting away with pocket fulls of Bitcoins. But what you don’t know is according to researches from Proofpoint, the Defray ransomeware technique is a major contributor.
Defray Ransomware: A Quick Intro
There have been various attacks against hospitals and schools over the past few years. Most of those ransomware distribution campaigns netted the criminals thousands of dollars, all of which was paid in Bitcoin. It now appears the criminals are back with a new tool, identified as Defray ransomware. It is quite a problematic development, even though there have only been two very small campaigns involving this malware so far.
The name “Defray” was not chosen randomly by researchers either. Though developers may have given it a different name, researchers refer to this family as Defray due to the name of the command & control server being used to communicate with the malware. This server appears to reside on the 000WebHostApp domain for the time being, although it may very well be taken down in the coming weeks. A centralized server makes it a bit easier for security researchers to combat ransomware outbreaks, even though it remains a tedious process.
Here’s How The Defray Ransomware Works
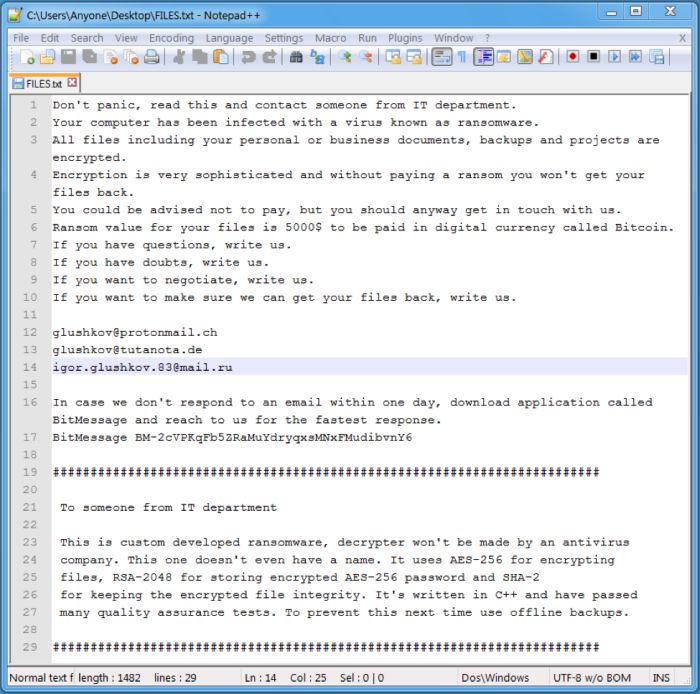
Once a victim downloads and executes a Microsoft Word attachment, the malware payload will be installed on the system. The victims will see a file called FILES.TXT in virtually every folder on their computer systems, which contains information on how they can restore file access. It appears victims are asked to get in touch with the criminals via email using one of three different email addresses. There is also an option to communicate through the BitMessage application if needed.
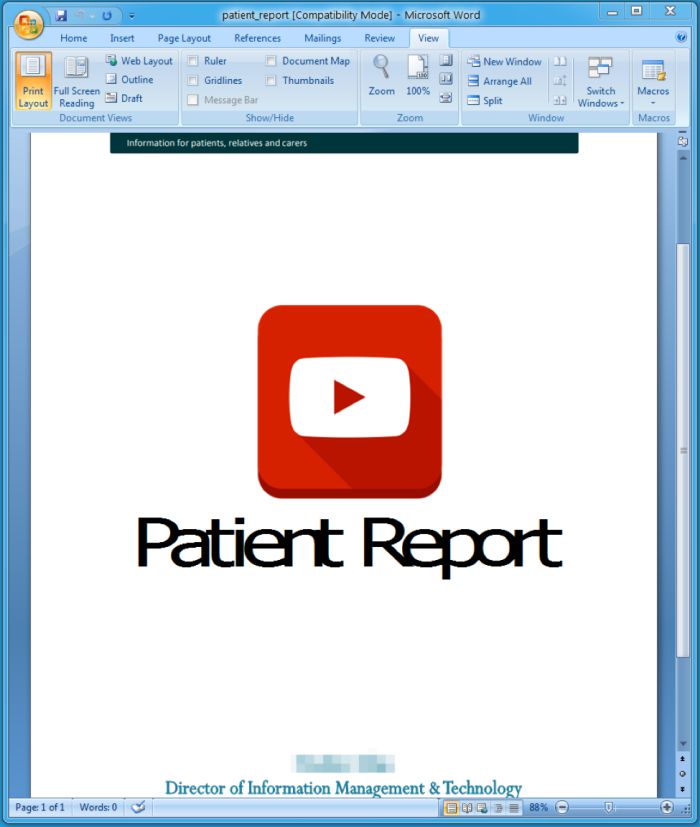
In the screenshot shown below, is an attachment received by a hospital and it uses a UK hospital logo in the upper right (not shown) and purports to be from the Director of Information Management & Technology at the hospital.
On another attack, on August 15 they targeted Manufacturing and Technology verticals and involving messages with the subject “Order/Quote” and a Microsoft Word document containing an embedded executable (also an OLE packager shell object).
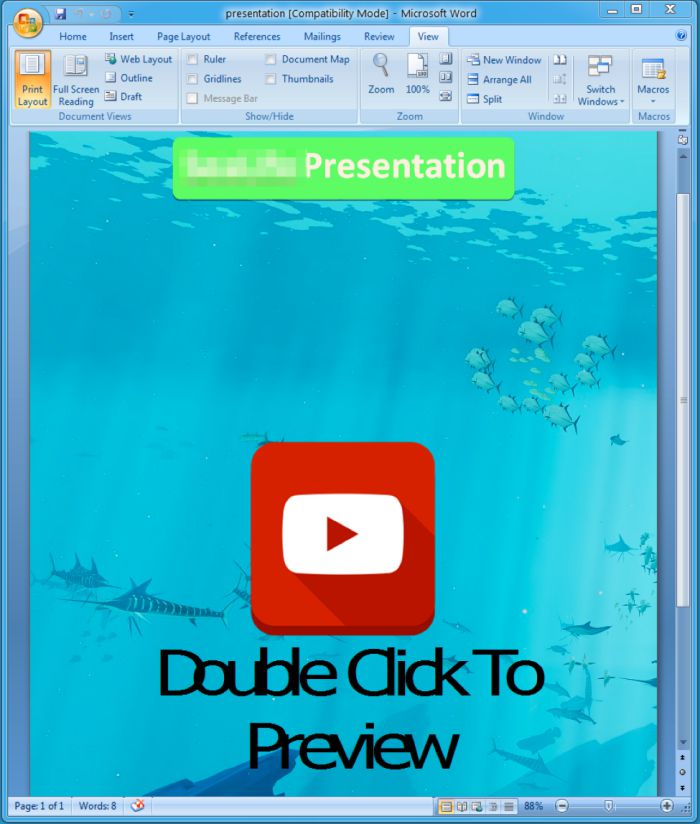
In the sample below the attackers used an attachment to lure unsuspicious victims where it referenced a UK-based aquarium with international locations (see screenshot below), and purported to be from a representative of the aquarium.
How To Verify You’ve Been Attacked
To alert the victim that their computer has been infected and that their files are encrypted, this ransomware creates FILES.TXT (screenshot below) in many folders throughout the system. HELP.txt, with identical content to FILES.txt, also appeared on the Desktop folder when the Proofpoint researches executed the ransomware.
What Are They Demanding (Bitcoin & Cents)
Right now, victims are asked to make a ransom payment of US$5,000 in Bitcoin. Given the current Bitcoin price, that means they will pay slightly over 1.15 BTC. Although the Bitcoin amount itself is pretty low, a US$5,000 payment is still quite substantial for any affected company. It may be possible to negotiate a smaller amount depending on how the communication with the criminals evolves. Interestingly, the ransom note also mentions how the infected victims should maintain offline backups of their files to prevent future attacks of this magnitude. This does feel like salt in the wound for victims.
In Conclusion
The Defray ransomware is a professionally developed ransomware strain. It is unclear if it uses any source code from other projects which have made a name in the past. The ransom note claims that this payload is custom-tailored to infect one’s particular system, which would make it incredibly difficult to come up with a free decryption tool. It is far less obnoxious compared to most malware attacks, which also makes it a much bigger threat for enterprises and companies in specific industries. It will be interesting to see if this malware is successful in the long run, though.
It is also likely that Defray is not for sale, either as a service or as a licensed application like many ransomware strains. Instead, it appears that Defray may be for the personal use of specific threat actors, making its continued distribution in small, targeted attacks more likely. We will continue to monitor this threat and provide updates as new information emerges.

